OPINION – Winning wars with algorithms and AI are not a futuristic concept but a present capability already determining outcomes in various conflict zones and military domains.
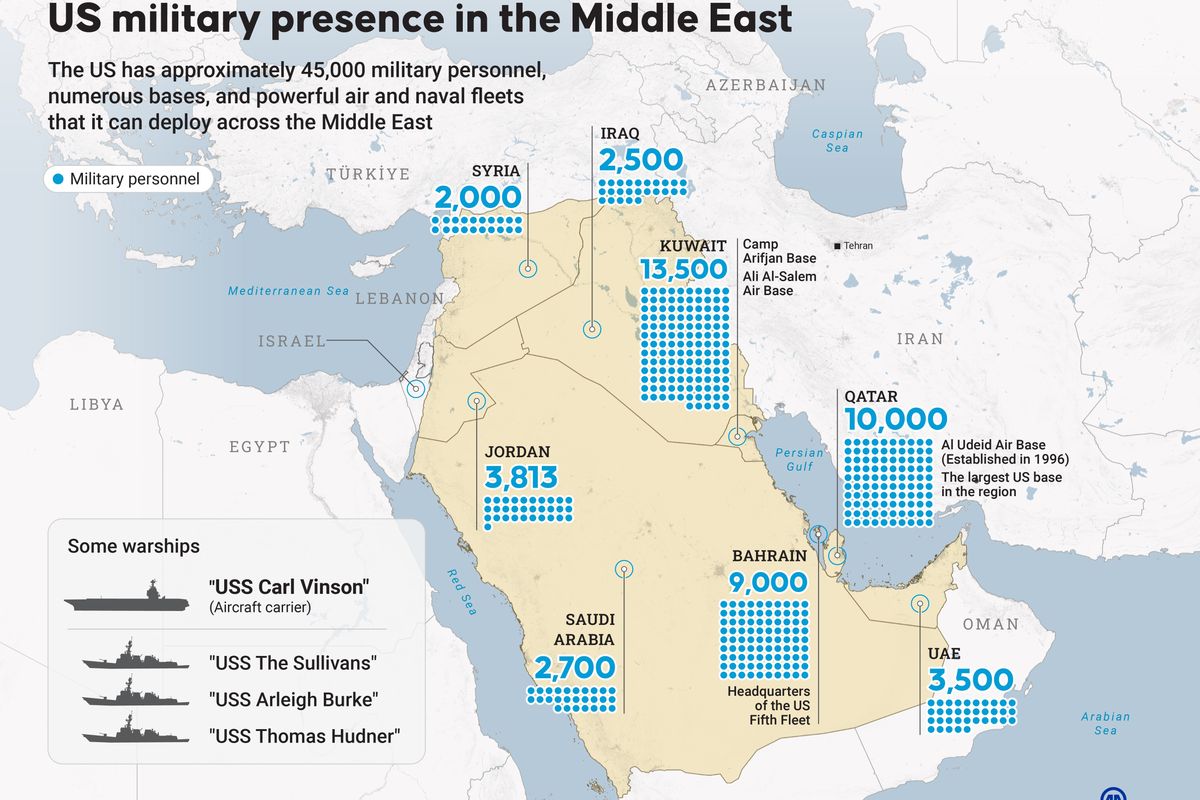
In late February 2024, the Department of Defense (DoD) announced that they used artificial intelligence (AI) to identify military targets hit by air strikes in Iraq and Syria marking a seminal moment in DoD’s targeting methodology. Project Maven – which leverages research on large language models and data labeling – is an AI intelligence tool designed to process imagery and full-motion video from unmanned aerial vehicles to automatically detect or identify potential targets. It was created in 2017 by the DoD and is a program of record at the National Geospatial-Intelligence Agency (NGA).
In 2023, NGA Director Vice Admiral Frank Whitworth confirmed that the agency was working with the “combatant commands to integrate AI into workflows, accelerating operations and speed-to-decision.”
After the October 2023 Hamas attack, the Israeli Defense Forces (IDF) turned to an AI tool that can quickly identify appropriate military targets and assist with target selection that filters into a Target ‘Bank’. Through Jerusalem Post reporting, we know the AI that was used to build out the Target Bank made significant contributions to IDF target discovery capabilities facilitating faster associations between targets and identifying new signatures or features of a target that led to qualitative updates to a target’s profile.
The Target Bank enabled the IDF to strike over 11,000 targets in Gaza between October 7 and November 2, 2023, and helped the IDF target and destroy 150 tunnels in one day, according to Jerusalem Post reporting. Their reporting also highlighted that the IDF went from identifying 10 targets in 10 days of work to 100 targets in the same amount of time – demonstrating a more efficient and faster transition from intelligence collection to intelligence targeting.
The Cipher Brief Threat Conference is happening October 5-8 in Sea Island, GA. The world's leading minds on national security from both the public and private sectors will be there. Will you? Apply for a seat at the table today.
Now that the public record shows that AI has been used for target development, the next evolution of this technology is already being pursued – fully autonomous weapons that can seek and select targets on their own without human operator interventions also known as lethal autonomous weapons systems (LAWS). While the AI drone competition between Ukraine’s Saker Scout and Russia’s Lancet has had mixed results and impact, the goal of developing a reliable platform that guides itself to a target without a human operator is inching closer to reality due to such conflicts acting as a test range. The race to develop LAWS is putting pressure on the U.S. and its allies to maintain a leading role in international technical discussion and forums on AI governance, rules, regulations and protocols.
China, eager to blunt the West’s attempts to shape AI technology and weapons development, has substantially invested more in its AI military program compared to the U.S. that is helping it build domestic partnerships with companies and academic institutions. China had over 50 companies and organizations at the 2024 Unmanned Systems conference in Abu Dhabi – a significantly larger presence than the U.S. – demonstrating its interest to lead in this tech space.
As countries transition to more unmanned systems and platforms, human involvement at the beginning of the target selection process will need accurate date and intelligence so that any autonomous capability using edge computing and algorithms will function within the parameters and constraints built into the programming. Frontloading human involvement or rules of engagement in such systems may not be enough when you consider glitches, hallucinations and bias can plague AI functionality. Determining how much human interaction from the “left of launch” to attack using LAWS will remain a critical feature for countries to consider. Balancing human judgement and control while not sacrificing the speed of the system will be critical.
Everyone needs a good nightcap. Ours happens to come in the form of a M-F newsletter that provides the best way to unwind while staying up to speed on national security. (And this Nightcap promises no hangover or weight gain.) Sign up today.
While Washington and Beijing may eventually hammer out an agreement on a framework for the responsible development and use of AI, particularly in military systems, the future battlefield is already taking shape into what will become smart skirmishes, smart conflicts or smart wars. The AI genie will never be put back in the bottle as it proliferates beyond any eventually signed accords and will continue to mature across the various land, air, maritime and cyber domains. Non-state actors will also benefit from AI advancements and technologies used for LAWS and cyber weapons that will add further complexity to any U.S. defensive posture. As the U.S. and its allies move closer to automated warfare scenarios and threats, the likelihood for unintended consequences could lead to a series of cascading events driven by AI’s speed.
That is why DoD’s Data, Analytics, and Artificial Intelligence Adoption Strategy and its Combined Joint All-Domain Command and Control (CJADC2) initiative will have to be successful if our military is to dominate in the AI battlespace.
The Cipher Brief is committed to publishing a range of perspectives on national security issues submitted by deeply experienced national security professionals.
Opinions expressed are those of the author and do not represent the views or opinions of The Cipher Brief.
Have a perspective to share based on your experience in the national security field? Send it to Editor@thecipherbrief.com for publication consideration.
Read more expert-driven national security insights, perspective and analysis in The Cipher Brief