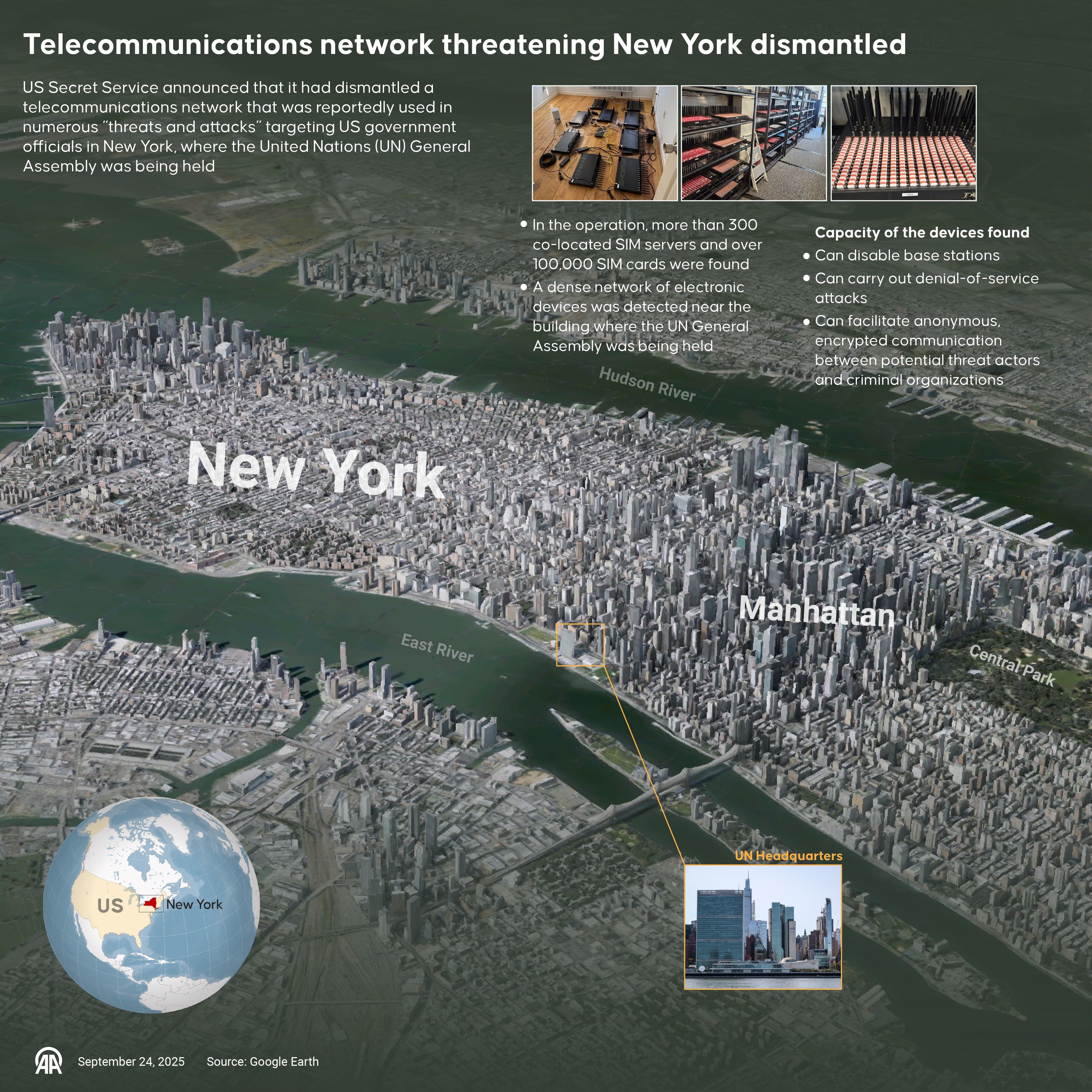
DEEP DIVE — When Secret Service agents swept into an inconspicuous building near the United Nations General Assembly late last month, they weren’t tracking guns or explosives. Instead, they dismantled a clandestine telecommunications hub that investigators say was capable of crippling cellular networks and concealing hostile communications.
According to federal officials, the operation seized more than 300 devices tied to roughly 100,000 SIM cards — an arsenal of network-manipulating tools that could disrupt the cellular backbone of New York City at a moment of geopolitical tension. The discovery, officials stressed, was not just a one-off bust but a warning sign of a much broader national security vulnerability.
The devices were designed to create what experts call a “SIM farm,” an industrial-scale operation where hundreds or thousands of SIM cards can be manipulated simultaneously. These setups are typically associated with financial fraud or bulk messaging scams. Still, the Secret Service warned that they can also be used to flood telecom networks, disable cell towers, and obscure the origin of communications.
In the shadow of the UN, where global leaders convene and security tensions are high, the proximity of such a system raised immediate questions about intent, attribution, and preparedness.
“(SIM farms) could jam cell and text services, block emergency calls, target first responders with fake messages, spread disinformation, or steal login codes,” Jake Braun, Executive Director of the Cyber Policy Initiative at the University of Chicago and former White House Acting Principal Deputy National Cyber Director, tells The Cipher Brief. “In short, they could cripple communications just when they’re needed most.”
Sign up for the Cyber Initiatives Group Sunday newsletter, delivering expert-level insights on the cyber and tech stories of the day – directly to your inbox. Sign up for the CIG newsletter today.
How SIM Farms Work
At their core, SIM farms exploit the fundamental architecture of mobile networks. Each SIM card represents a unique identity on the global communications grid. By cycling through SIMs at high speed, operators can generate massive volumes of calls, texts, or data requests that overwhelm cellular infrastructure. Such floods can mimic the effects of a distributed denial-of-service (DDoS) attack, except the assault comes through legitimate carrier channels rather than obvious malicious traffic.
“SIM farms are essentially racks of modems that cycle through thousands of SIM cards,” Dave Chronister, CEO of Parameter Security, tells The Cipher Brief. “Operators constantly swap SIM cards and device identifiers so traffic appears spread out rather than coming from a single source.”
That makes them extremely difficult to detect.
“They can mimic legitimate business texts and calls, hide behind residential internet connections, or scatter equipment across ordinary locations so there’s no single, obvious signal to flag,” Chronister continued. “Because SIM farms make it hard to tie a number back to a real person, they’re useful to drug cartels, human-trafficking rings and other organized crime, and the same concealment features could also be attractive to terrorists.”
That ability to blend in, experts highlight, is what makes SIM farms more than just a criminal nuisance.
While SIM farms may initially be used for financial fraud, their architecture can be easily repurposed for coordinated cyber-physical attacks. That dual-use nature makes them especially appealing to both transnational criminal groups and state-backed intelligence services.
Who Might Be Behind It?
The Secret Service, however, has not publicly attributed the network near the UN to any specific individual or entity. Investigators are weighing several possibilities: a transnational fraud ring exploiting the chaos of UN week to run large-scale scams, or a more concerning scenario where a state-backed group positioned the SIM farm as a contingency tool for disrupting communications in New York.
Officials noted that the operation’s sophistication suggested it was not a low-level criminal endeavor. The hardware was capable of sustained operations against multiple carriers, and its sheer scale — 100,000 SIM cards — far exceeded the typical scale of fraud schemes. That raised the specter of hostile governments probing U.S. vulnerabilities ahead of potential hybrid conflict scenarios.
Analysts note that Russia, China, and Iran have all been implicated in blending criminal infrastructure with state-directed cyber operations. Yet, these setups serve both criminals and nation-states, and attribution requires more details than are publicly available.
“Criminal groups use SIM farms to make money with scams and spam,” said Braun. “State actors can use them on a bigger scale to spy, spread disinformation, or disrupt communications — and sometimes they piggyback on criminal networks.”
One source in the U.S. intelligence community, who spoke on background, described that overlap as “hybrid infrastructure by design.”
“It can sit dormant as a criminal enterprise for years until a foreign government needs it. That’s what makes it so insidious,” the source tells The Cipher Brief.
From Chronister’s purview, the “likely explanation is that it’s a sophisticated criminal enterprise.”
“SIM-farm infrastructure is commonly run for profit and can be rented or resold. However, the criminal ecosystem is fluid: nation-states, terrorist groups, or hybrid actors can and do co-opt criminal capabilities when it suits them, and some state-linked groups cultivate close ties with criminal networks,” he said.
The Broader National Security Blind Spot
The incident during the United Nations General Assembly also underscores a growing blind spot in U.S. protective intelligence: telecommunications networks as contested terrain. For decades, federal resources have focused heavily on cybersecurity, counterterrorism, and physical threats. At the same time, the connective tissue of modern communications has often been treated as a commercial domain, monitored by carriers rather than security agencies.
The Midtown bust suggests that assumption no longer holds. The Secret Service itself framed the incident as a wake-up call.
“The potential for disruption to our country’s telecommunications posed by this network of devices cannot be overstated,” stated U.S. Secret Service Director Sean Curran. “The U.S. Secret Service’s protective mission is all about prevention, and this investigation makes it clear to potential bad actors that imminent threats to our protectees will be immediately investigated, tracked down and dismantled.”
However, experts warn that U.S. defenses remain fragmented. Carriers focus on fraud prevention, intelligence agencies monitor foreign adversaries, and law enforcement investigates domestic crime. The seams between those missions are precisely where SIM farms thrive.
The Cipher Brief brings expert-level context to national and global security stories. It’s never been more important to understand what’s happening in the world. Upgrade your access to exclusive content by becoming a subscriber.
Hybrid Warfare and the Next Front Line
The rise of SIM farms reflects the evolution of hybrid warfare, where the boundary between criminal activity and state action blurs, and adversaries exploit commercial infrastructure as a means of attack. Just as ransomware gangs can moonlight as proxies for hostile intelligence services, telecom fraud networks may double as latent disruption tools for foreign adversaries.
Additionally, the threat mirrors patterns observed abroad. In Ukraine, officials have reported Russian operations targeting cellular networks to disrupt battlefield communications and sow panic among civilians. In parts of Africa and Southeast Asia, SIM farms have been linked to both organized crime syndicates and intelligence-linked influence campaigns.
That same playbook, experts caution, could be devastating if applied in the heart of a global city.
“If activated during a crisis, such networks could flood phone lines, including 911 and embassy hotlines, to sow confusion and delay coordination. They can also blast fake alerts or disinformation to trigger panic or misdirect first responders, making it much harder for authorities to manage an already volatile situation,” Chronister said. “Because these setups are relatively cheap and scalable, they are an inexpensive but effective way to complicate emergency response, government decision-making, and even protective details.”
Looking Ahead
The dismantling of the clandestine telecom network in New York may have prevented an imminent crisis, but experts caution that it is unlikely to be the last of its kind. SIM farms are inexpensive to set up, scalable across borders, and often hidden in plain sight. They represent a convergence of cyber, criminal, and national security threats that the U.S. is only beginning to treat as a unified challenge.
When it comes to what needs to be done next, Braun emphasized the importance of “improving information sharing between carriers and government, investing in better tools to spot hidden farms, and moving away from SMS for sensitive logins.”
“Treat SIM farms as a national security threat, not just telecom fraud. Limit access to SIM farm hardware and punish abuse. Help smaller carriers strengthen defenses,” he continued. “And streamline legal steps so takedowns happen faster.”
Chronister acknowledged that while “carriers are much better than they were five or ten years ago, as they’ve invested in spam filtering and fraud analytics, attackers can still get through when they rotate SIMs quickly, use eSIM provisioning, or spread activity across jurisdictions.”
“Law enforcement and intelligence have powerful tools, but legal, technical, and cross-border constraints mean detection often outpaces confident attribution and rapid takedown. Make it harder to buy and cycle through SIMs in bulk and strengthen identity verification for phone numbers,” he added. “Require faster, real-time information-sharing between carriers and government during traffic spikes, improve authentication for public alerts, and run regular stress-tests and red-team exercises against telecom infrastructure. Finally, build joint takedown and mutual-assistance arrangements with allies so attackers can’t simply reconstitute operations in another country.”
Are you Subscribed to The Cipher Brief’s Digital Channel on YouTube? There is no better place to get clear perspectives from deeply experienced national security experts.
Read more expert-driven national security insights, perspective and analysis in The Cipher Brief because National Security is Everyone’s Business.